We’ve blogged a lot about how user security and privacy is at the heart of GOV.UK Verify. We’ve also talked about the Privacy and Consumer Advisory Group (PCAG) and one of their key outputs: the Identity Assurance Principles.
The Identity Assurance Principles ensure that identity systems - like GOV.UK Verify - are fair, balanced and operate for the user’s benefit.
But what do the principles really mean, and how do we implement them within the GOV.UK Verify journey? This blog post is the second in a series of 3 where we’ll take a look at each of the 9 principles and explain what they mean for our users.
Part one of this series covered user control, transparency and multiplicity. Today we cover the principles of data minimisation, data quality and service user access and portability.
Principle 4: Data Minimisation

My interactions only use the minimum data necessary to meet my needs.
This principle is about how there should be no unnecessary data collection, storage or sharing. GOV.UK Verify supports this by being a federated model that limits the information which government and any certified company holds to a minimum. Neither one has the whole picture, and each only have the information they need.
For example, at the start of the GOV.UK Verify journey users are asked a few simple questions in the hub. Based on their answers, the user is then presented with certified companies most likely to be able to verify their identity. The user cannot be identified based on the answers given.
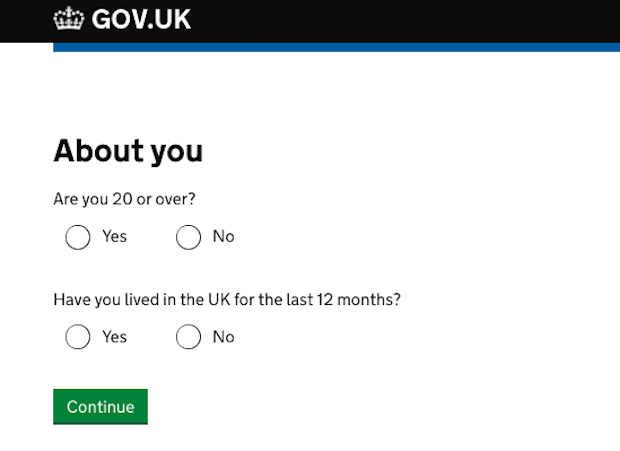
When the user goes on to create an identity account with their chosen certified company, the company collects the minimum amount of data that’s required to verify the user’s identity to the defined level of assurance the government service needs.
Whenever a user then signs into their identity account with their chosen certified company to access a government service, only the Matching Data Set is passed to the government service via the hub. The data that was used in the initial verification checks is not passed through.
Principle 5: Data Quality

I choose when to update my records.
This principle is about how certified companies should enable users to check and update the data that’s held about them at any time they wish simply, easily and free of charge.
GOV.UK Verify users can update the data that they have provided to the certified company by logging into their certified company identity account. Once logged in they are able to, for example: view and manage their basic personal information, view or amend their sign in options and see their account use history. An online account gives users the freedom to update their details, at any time, without needing to go in-store or contacting a call centre.
Principle 6: Service User Access and Portability

I have to be provided with copies of all my data on request. I can move/remove my data whenever I want.
Building on Principle 5, Principle 6 allows GOV.UK Verify users to receive copies of their data upon request and check and update data that’s held about them.
The simplest way for users to see the data that’s held about them by a certified company is by logging into their identity account.
Users can remove their personal data from a certified company by closing their account. However, the certified companies are required to keep audit records for 7 years. This is so that they can be used if there is a transactional dispute and the data is required for legal investigation.
What do you think?
So that’s how we apply principles of data minimisation, data quality and service user access and portability. What’s your view? Could we be doing more? Let us know in the comments below.
We’ll be publishing the next and last post in this series soon. Subscribe to the blog so you don’t miss the next installment.

2 comments
Comment by MarkK posted on
4. Data minimization has long been a principle for all under the data protection act, so hardly counts as special here. 6. Subject access requests are also normal fare for Data Protection, as is the obligation to correct errors in records.
5. Service available 24 hours a day - good, but hardly unusual online.
So what data can be changed? Changes of name and address clearly are needed somehow - to the assurance level noted in GPG43 - but (online) evidence/corroboration of a new address may be scant. Surely the user can't simply still have an assured ID higher than LoA1 if they can change everything (perhaps except date of birth) at will? How does change of name and/or address work, or is the typical user then excommunicated?
Comment by Emily Ch'ng posted on
Hi Mark,
Please see our IPV Operations Manual (redacted) as this has the details contained there to help answer your query: https://www.gov.uk/government/publications/govuk-verify-ipv-operations-manual-redacted