GOV.UK Verify developers: how our team works

...transfer skills throughout the team. It also produces high quality, maintainable code. In situations where it doesn't make sense to pair, we ensure peer review as a minimum to see...

...transfer skills throughout the team. It also produces high quality, maintainable code. In situations where it doesn't make sense to pair, we ensure peer review as a minimum to see...
...second step can be a code sent to a mobile phone (one of the more commonly used methods), or it can be another method such as a code communicated to...
...shared library of code used for our SAML (Security Assertion Markup Language) messages. This removes dependencies between our microservices and will allow us to make changes to our code faster....
...effectively. To continue keeping GOV.UK Verify available and secure we’ve: started automating lengthy steps in our process when releasing code to our live environment upgraded lots of applications and libraries...

...step such as having a one-off code sent to your mobile phone or generating a code in an authentication app. Therefore, if your information is lost or compromised it will...

...to agile best practices. With our current structure, I believe we’ve achieved these goals. Scaling Agile for GOV.UK Verify’s governance Below is a diagram that illustrates our governance structure. At...
...covering security, Agile methodologies, open source code and more. The process was resource-intensive but it helped to focus the team on the requirements of the live assessment and proved a...
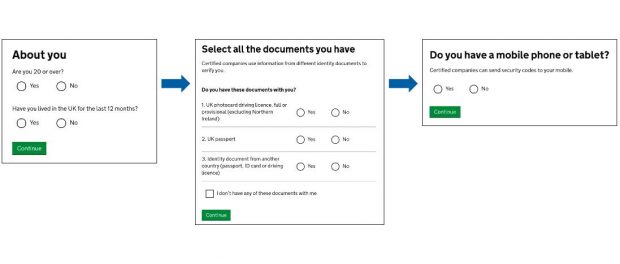
...be able to verify their identity. Asking questions in the best way, so users don’t waste their time The hub asks 3 sets of questions. Until recently, the questions appeared...
...old, unused code which reduces the time needed to release updates improved the reliability of our system monitoring dashboards Things we plan to do next In the coming 2 to...

...For the first exercise we did the ‘Minisculus Challenge’. This is a set of small coding puzzles based around codebreaking. We ran the exercises in a mob programming style, swapping...