Releasing safe and useful code for GOV.UK Verify
...to why this cannot be done for specific subsets of the source code). This post is about how we’re going to open up our code. It explains what we’ve opened...

...to why this cannot be done for specific subsets of the source code). This post is about how we’re going to open up our code. It explains what we’ve opened...

...that we operate that help the federation to run smoothly and securely. This is also something that is considered under Point 6 of the Digital by Default Service Standard assessment...
...do publish information about our design, but we don’t publish code that would reveal specifics about our implementation of the design. As James explains, 'we don’t publish information about the...
...app to generate a security code or to receive a security code on your landline phone, rather than waiting for a text to arrive, so you don’t need a mobile...
...debt. Here’s what we’ve been working on since the last update, and what we plan to do next. Increasing adoption of GOV.UK Verify We want departments across government to adopt...

...now more than 24,000 different combinations of 32 different data sources that can be used to verify an identity, depending on what evidence the individual chooses to provide and what...
...reducing our technical debt. Here’s what we’ve been working on since the last update, and what we plan to do next. Increasing adoption of GOV.UK Verify We want departments across...
...that evidence to make sure it’s valid and / or genuine (element B), establishing that the person owns the identity (element C), checking whether the identity registration might be fraudulent...
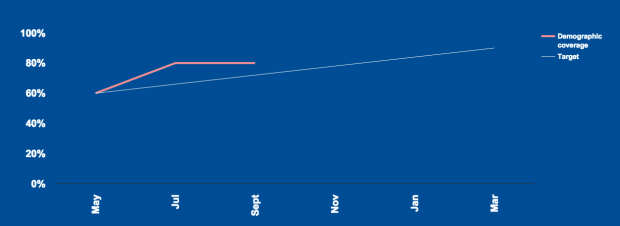
...been working on since our last update back in September and what we plan to do next. Improving the completion rate To improve the volume of visits that result in...

...will outline the commitments and resources that local councils will need to participate in our pilots, in addition to outlining what GDS will contribute. If you’re reading this from a...