Point 9 of the Digital by Default Service Standard says:
Use open standards and common government platforms where available.
GOV.UK Verify doesn’t just use open standards - we have helped set the standards for identity proofing and verification and online authentication for UK government digital services. These documents are jointly published by the Cabinet Office and CESG, the National Technical Authority for Information Assurance. All the certified companies are required to meet those standards, and have to be independently certified to confirm that they do.
The good practice guides have been designed to mitigate a range of specific identity fraud risks. In this post I’m going to going describe what we mean by identity fraud and explain some of the kinds of fraud GOV.UK Verify’s standards are designed to help prevent.
Impostors
GOV.UK Verify aims to stop others pretending to be you when accessing government services. We call someone that attempts to do this an ‘impostor’. They may try to register with one of the GOV.UK Verify certified companies using stolen identity information.
The many data breaches that have occurred over the last few years mean that a lot of stolen personal data is circulating online. In fact, this information can be bought for very little money by criminals using online criminal marketplaces. Below is a screenshot from an active criminal marketplace offering to sell the personal data of a UK resident including their credit card and bank details.
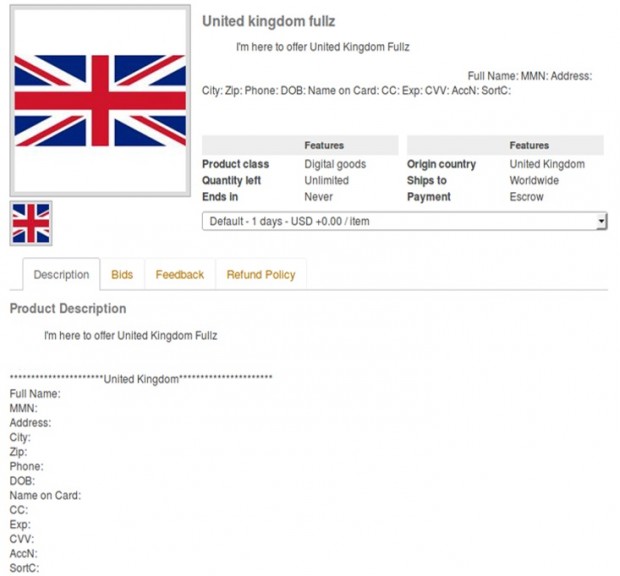
Our guidance on identity proofing and verification explains how the good practice guides require certified companies to carry out a range of checks to prevent someone using this kind of stolen information to successfully access services using your identity.
These checks cover 5 different elements of identity assurance, including making sure there is evidence that the identity exists (element A), validating that evidence to make sure it’s valid and / or genuine (element B), establishing that the person owns the identity (element C), checking whether the identity registration might be fraudulent (element D) and establishing that the identity has been active over time (element E).
As part of our guidance we require that the certified companies also check to see if your identity is known to have been used by an impostor in the past. If this is the case then they will take extra care to ensure that it is really you and not an impostor.
Account takeover
Because of the range of different checks certified companies are required to carry out, it’s quite difficult to create a false identity or steal someone else’s in order to create a GOV.UK Verify account. Criminals may attempt to bypass the registration process and instead try to get access to a verified identity account that has already been set up. We call this ‘account takeover’. The objective is to access the account you’ve created with a certified company and use it to interact with government services.
Usernames and passwords for many online services are available to buy from the dark web, mostly gained from one of the data breaches mentioned earlier. People tend to pick predictable passwords and use the same one across many web sites. If you do that, the cyber criminal doesn’t need to get hold of your username and password for a specific web site. They just need one of your passwords for a single service to work out what your passwords are for other services.
The guidance we give on authentication sets out the things we expect the certified companies to do to prevent this kind of attack from being successful. The certified companies offer a range extra security measures that means every sign in is unique: you wouldn’t be able to access an account just using a stolen username and password, you would also need to complete another step such as having a one-off code sent to your mobile phone or generating a code in an authentication app. Therefore, if your information is lost or compromised it will not give the attacker the capability to access to your account.
To get around this, criminals may try to use the account recovery processes to change your login details to something they know. The certified companies have to provide a way for you to access your account if you have forgotten your sign-in details. The certified companies are required to have measures in place to make sure if someone is trying to reset their sign-in details it is really the owner of the account and not someone else. For example, they might ask some security questions based on information you provided when you first create your account or ask you to provide some other proof of your identity.
Hijacking
Cyber criminals may not even try to attack your verified identity account with a certified company, but may instead target your computer, tablet or smartphone. They will try to install malicious software (malware) on your device that will let them intercept and interfere with your internet use. This way they can let you sign in as usual, but behind the scenes they can perform actions using your account that you are completely unaware of. We call this ‘hijacking’.
Adam has already written about how we keep GOV.UK Verify secure and protect you from loss of data. Although hijacking is less identity related and more technical, we still count this as ‘identity enabled’ fraud since the criminal is misusing your identity account for their own gain.
GOV.UK Verify, the certified companies and the connected government services try to spot hijacking occuring using a range of technologies but it is incredibly difficult. The most effective protection against this attack is for you to have good quality anti-virus software on your device and keeping it, your operating system, and other software up to date.
Continuous improvement
The controls we have built in to GOV.UK Verify and the standards we’ve set for identity assurance mean the service is resilient to a wide range of identity related crime. However, we’re always working to improve the way we work, respond to new and evolving threats and take advantage of the most up to date ways to help protect users of GOV.UK Verify from identity fraud.
We work with colleagues across government and with law enforcement partners who have a current understanding of identity crime and the potential threats to the delivery of online services. This helps us to maintain an up to date understanding of the types of fraud that are being attempted and the methods being used.
We keep the good practice guides constantly under review. We update them regularly to make sure they reflect the evolving and changing ways in which identity fraudsters look to undertake their criminal behaviour.
Keep up to date with the latest news by signing up for email updates or follow @GOVUKVerify on Twitter.

2 comments
Comment by Tim Coote posted on
How are you verifying the design and implementation?
How much of a conflict of interest is there in having GCHQ design the approach, bearing in mind the way that NSA has tried to influence NIST in the past?
Comment by Rebecca Hales posted on
Hi Tim
We constantly monitor the threats and attacks in order to understand the effectiveness of the controls. We have blogged about the requirements certified companies have to meet to ensure they are implementing the controls properly. See the following posts:
https://identityassurance.blog.gov.uk/2015/07/17/gov-uk-verify-making-sure-certified-companies-are-ready-to-connect/
https://identityassurance.blog.gov.uk/2014/12/11/what-it-means-to-be-a-certified-company/
CESG were one of many stakeholders whose views were taken into account during the drafting and design of the process.