Services planning to use GOV.UK Verify - update

We posted in October listing some of the services we were expecting to start using GOV.UK Verify between October 2014 and March 2015. This post provides an update on our...

We posted in October listing some of the services we were expecting to start using GOV.UK Verify between October 2014 and March 2015. This post provides an update on our...
...to use. The bidder must list each of the datasets it proposes to use to fulfil elements A to E of the Identity Proofing and Verification (IPV) requirements, as defined...
...for the first time, you’ll be asked to choose from a list of certified companies (also known as ‘identity providers’ - they can actually be any type of organisation that...
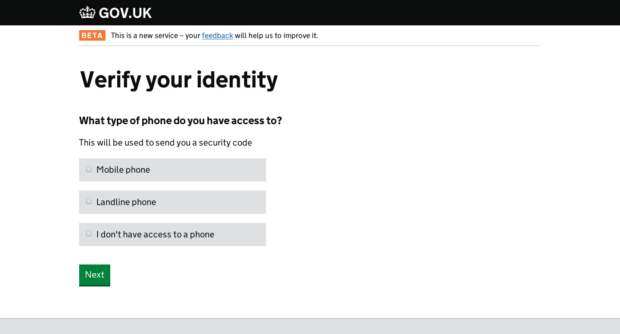
...need to do if they wanted to choose another provider from the list. Screenshot from our new user interface - showing which certified company is most likely to be able...
We’ve been working with departments to identify the digital services that will need to use GOV.UK Verify. This post lists the services we’re expecting to start using GOV.UK Verify in...

...and keyboard while the rest of the mob act as ‘navigators’ by suggesting what source code needs to be produced. Not everybody will be part of the mob at all...
...pages (e.g. clicks made on links) and extra tagging code called custom variables which enabled us to segment the data. We also added an extra step into the process: when...
...Commissioner’s Code of Practice for Privacy Impact Assessments provides an excellent proposed methodology for a PIA, which was used as a starting point for the review of GOV.UK Verify. Conducting...
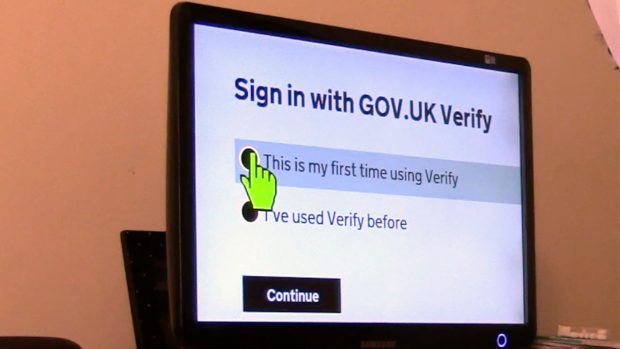
...to quickly get an overview of the important content on a page, rather than having to listen to it all in sequence. Often people using screen readers do this by...
...covering security, Agile methodologies, open source code and more. The process was resource-intensive but it helped to focus the team on the requirements of the live assessment and proved a...