Research and Analytics Working Closer Together
...pages (e.g. clicks made on links) and extra tagging code called custom variables which enabled us to segment the data. We also added an extra step into the process: when...

...pages (e.g. clicks made on links) and extra tagging code called custom variables which enabled us to segment the data. We also added an extra step into the process: when...

...and keyboard while the rest of the mob act as ‘navigators’ by suggesting what source code needs to be produced. Not everybody will be part of the mob at all...
...we’ve automated most of our code release process and are now setting up metrics to measure where we can make further improvements in speed and reliability. Things we plan to...
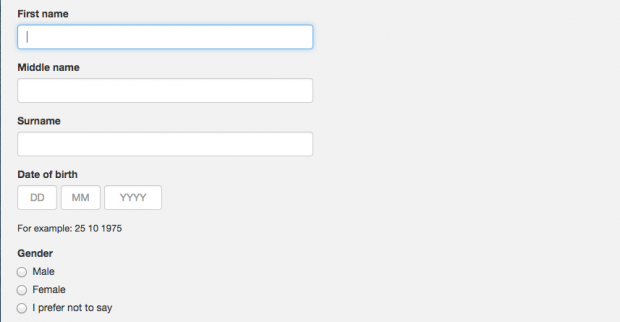
...it’s best practice to always ask for gender. GOV.UK Verify makes gender optional as, whilst it is not essential for matching, it can make it more successful. Keep up to...
...the identity provider. If the Privacy and Consumer Advisory Group needs to update the Identity Assurance Principles - for example, in response to changes in best practice, or to address...
...eID reuse. This means analysing existing standards and applying best practice to the current architecture to define requirements for a production ready version of STORK. Benefits of STORK for the...
...is only available on a limited basis and we may decide to end the trial before the self-assessment deadline on Saturday, if we think that’s the best thing to do...

...so that we can be sure their solutions are secure, meet the standards and are well designed. The aim is to offer users a choice of companies that best meet...
...information, showing empathy when our users share feedback, and competence when they want answers. We look to the GDS Social Media Playbook for guidance on best practice and follow the...
...will help us develop a shared understanding of the needs for identity assurance, and how we can best work with our private sector colleagues as the market develops to meet...