Using mobile phones as part of GOV.UK Verify
...we expect they will use a range of methods. Identity providers have to include 2 steps to authenticate users - a secret known only to the user (eg a password),...
...we expect they will use a range of methods. Identity providers have to include 2 steps to authenticate users - a secret known only to the user (eg a password),...
...combinations of things users have, we need to compare this to the combinations of things certified companies can use to verify users. The number of different combinations will grow over...
...service they want to use. tested new prototypes of the user journey in our user research lab. We wanted to see if there are ways of communicating the concept in...
...a user creating or re-using a verified account with a certified company, we’ve: started investigating the technical possibility of helping users to pause their identity verification journey for them to...
...which they use the internet - and online government services - more deeply. This also meant that we could see any assistive technology exactly as the participant used it in...
...of development but no exposure to real users. The main constraint on who can use GOV.UK Verify right now is the range of evidence we can allow people to use...

...see how our work affects users and keep the GDS mantra "What is the user need?" at the top of our minds. We ask each member of the delivery team...
...sources will only be used on the basis of informed user choice and consent. Encouraging certified companies to use a wider range of good quality, relevant data sources - our...

...they need to be sure they are dealing with the correct user - we’ll announce details of these services in the coming weeks. This will also allow users to re-use...

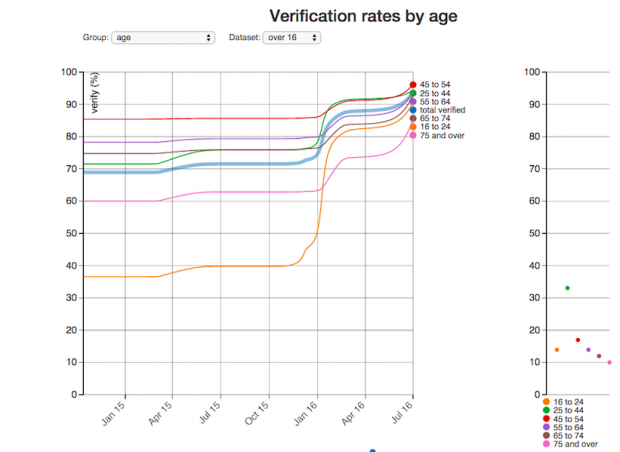
...the verification process successfully. The success rate can also be increased by improving and iterating the user experience to make it as straightforward as possible for people to use the...